In the modern landscape of software development, security is not an afterthought; it’s a foundational pillar. For developers in the Java ecosystem, understanding and implementing robust authentication mechanisms is crucial, especially with the rise of distributed systems, Java Microservices, and complex Java REST API architectures. Authentication, the process of verifying a user’s identity, is the first line of defense in protecting sensitive data and application resources.
This article provides a deep dive into Java Authentication, charting a course from its traditional roots to the sophisticated, framework-driven approaches used in today’s Java Development. We will explore the foundational Java Authentication and Authorization Service (JAAS), transition to the de-facto standard for modern applications, Spring Security, and delve into stateless authentication using JSON Web Tokens (JWT). Whether you are a seasoned professional working with Java Enterprise systems or a developer just starting with Spring Boot, this guide will equip you with the knowledge and practical code examples to build secure and reliable Java applications.
Understanding the Core: Java Authentication and Authorization Service (JAAS)
Before modern frameworks simplified security, the Java platform provided a standard, pluggable mechanism for authentication and authorization: JAAS. Part of the core Java Security architecture since JDK 1.4, JAAS decouples authentication logic from the application code, allowing different authentication technologies to be plugged in without changing the application itself.
What is JAAS?
JAAS is built around a few key concepts that form the basis of its Pluggable Authentication Module (PAM) framework:
- Subject: Represents the source of a request, such as a user. A Subject can have multiple identities (Principals).
- Principal: Represents a specific identity for a Subject (e.g., a username or a user ID).
- Credential: Contains security-related data for a Subject, such as passwords, Kerberos tickets, or public key certificates.
- LoginModule: The core component where the actual authentication work happens. You can implement custom
LoginModules for different authentication schemes (e.g., database, LDAP, Kerberos). - LoginContext: The application’s entry point into the JAAS framework. It reads a configuration, instantiates the specified
LoginModules, and coordinates the authentication process.
While powerful, JAAS can be verbose and complex to configure for web applications, which is why frameworks like Spring Security have become more popular for Java Web Development.
A Practical JAAS LoginModule Example
To understand how JAAS works, let’s look at a simple LoginModule that authenticates a user against a hardcoded username and password. This illustrates the fundamental contract a developer must implement.
package com.example.jaas;
import javax.security.auth.Subject;
import javax.security.auth.callback.*;
import javax.security.auth.login.LoginException;
import javax.security.auth.spi.LoginModule;
import java.io.IOException;
import java.util.Map;
public class SimpleLoginModule implements LoginModule {
private Subject subject;
private CallbackHandler callbackHandler;
private String username;
private boolean loginSucceeded = false;
@Override
public void initialize(Subject subject, CallbackHandler callbackHandler,
Map<String, ?> sharedState, Map<String, ?> options) {
this.subject = subject;
this.callbackHandler = callbackHandler;
}
@Override
public boolean login() throws LoginException {
NameCallback nameCallback = new NameCallback("Username: ");
PasswordCallback passwordCallback = new PasswordCallback("Password: ", false);
try {
callbackHandler.handle(new Callback[]{nameCallback, passwordCallback});
username = nameCallback.getName();
char[] password = passwordCallback.getPassword();
passwordCallback.clearPassword();
// In a real application, you would check against a database or LDAP
if ("admin".equals(username) && "password123".equals(new String(password))) {
System.out.println("Authentication successful!");
loginSucceeded = true;
return true;
} else {
System.out.println("Authentication failed.");
loginSucceeded = false;
throw new LoginException("Authentication failed");
}
} catch (IOException | UnsupportedCallbackException e) {
throw new LoginException(e.getMessage());
}
}
@Override
public boolean commit() throws LoginException {
if (!loginSucceeded) {
return false;
}
// Add the principal to the subject
subject.getPrincipals().add(new SimplePrincipal(username));
return true;
}
// Abort and logout methods are used to clean up state
@Override
public boolean abort() throws LoginException {
if (!loginSucceeded) {
return false;
}
logout();
return true;
}
@Override
public boolean logout() throws LoginException {
subject.getPrincipals().removeIf(p -> p instanceof SimplePrincipal);
loginSucceeded = false;
username = null;
return true;
}
}
// A simple Principal implementation
class SimplePrincipal implements java.security.Principal {
private final String name;
public SimplePrincipal(String name) { this.name = name; }
@Override
public String getName() { return name; }
// Implement equals and hashCode
}
This code demonstrates the two-phase commit process of JAAS (login and commit). While foundational, modern Java Frameworks provide higher-level abstractions that are easier to manage.
Simplifying Security: Modern Authentication with Spring Security




For modern Java Backend development, especially when using Spring Boot, Spring Security is the undisputed leader. It provides a comprehensive and highly customizable authentication and access-control framework. It completely abstracts away the complexities of underlying mechanisms like JAAS and provides a simple, fluent API for securing applications.
Why Spring Security?
Spring Security excels by integrating deeply into the Spring ecosystem. It leverages a chain of servlet filters to intercept requests and apply security rules. Key benefits include:
- Comprehensive Protection: Handles authentication, authorization, CSRF protection, session management, and more out of the box.
- Extensibility: Easily customizable to support various authentication mechanisms, from form-based login and Basic Auth to OAuth2 and JWT.
- Framework Integration: Seamlessly secures Spring MVC/WebFlux endpoints, making it ideal for building a secure Java REST API.
Implementing Basic Authentication in a Spring Boot REST API
Let’s configure a simple in-memory authentication for a Spring Boot application. This is a great starting point for development and testing. All you need is a single configuration class.
package com.example.security;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.core.userdetails.User;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder;
import org.springframework.security.crypto.password.PasswordEncoder;
import org.springframework.security.provisioning.InMemoryUserDetailsManager;
import org.springframework.security.web.SecurityFilterChain;
import static org.springframework.security.config.Customizer.withDefaults;
@Configuration
@EnableWebSecurity
public class BasicAuthSecurityConfig {
@Bean
public SecurityFilterChain filterChain(HttpSecurity http) throws Exception {
http
.authorizeHttpRequests(authz -> authz
.requestMatchers("/api/public/**").permitAll() // Public endpoints
.requestMatchers("/api/admin/**").hasRole("ADMIN") // Admin-only endpoints
.anyRequest().authenticated() // All other requests need authentication
)
.httpBasic(withDefaults()) // Enable HTTP Basic Authentication
.csrf(csrf -> csrf.disable()); // Disable CSRF for stateless APIs
return http.build();
}
@Bean
public UserDetailsService userDetailsService() {
UserDetails user = User.builder()
.username("user")
.password(passwordEncoder().encode("password"))
.roles("USER")
.build();
UserDetails admin = User.builder()
.username("admin")
.password(passwordEncoder().encode("adminpass"))
.roles("ADMIN", "USER")
.build();
return new InMemoryUserDetailsManager(user, admin);
}
@Bean
public PasswordEncoder passwordEncoder() {
return new BCryptPasswordEncoder();
}
}
In this example, we define a SecurityFilterChain bean, which is the modern way to configure Spring Security in Java 17 and newer. We specify URL patterns, permit some, and require authentication for others. The UserDetailsService bean provides user credentials—here, from memory, but in a real application, this would connect to a database via JPA or JDBC. Finally, we define a PasswordEncoder, a critical component for securely storing passwords.
Advanced Java Authentication: Stateless APIs with JWT and OAuth2
In a Java Microservices architecture, stateful, session-based authentication can be a bottleneck. Stateless authentication, where each request contains all necessary information for the server to verify the user, is the preferred approach. This is where JSON Web Tokens (JWT) shine.
The Rise of Token-Based Authentication
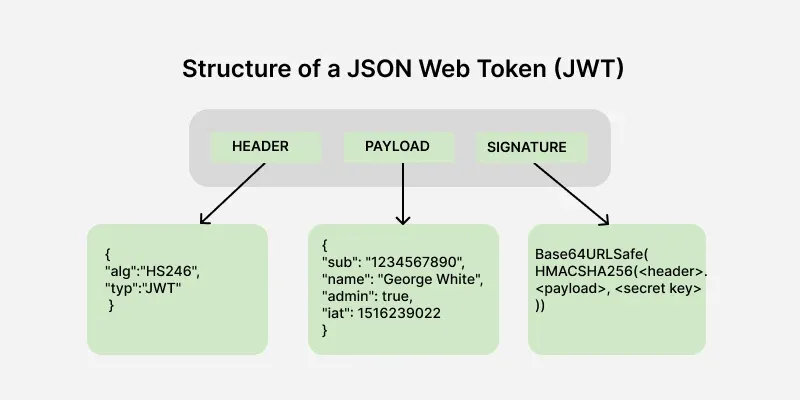
A JWT is a compact, URL-safe means of representing claims to be transferred between two parties. It’s a signed JSON object that consists of three parts: a header, a payload, and a signature. The signature ensures the token’s integrity, proving it hasn’t been tampered with. This makes JWT Java implementations perfect for securing communication between services.
Implementing JWT Authentication in Spring Boot
To add JWT support to our Spring Boot application, we need a way to generate tokens upon successful login and a filter to validate tokens on subsequent requests. We’ll use the popular `io.jsonwebtoken:jjwt` library, which can be added via Java Maven or Java Gradle.








First, a service to create and validate tokens:
package com.example.security.jwt;
import io.jsonwebtoken.Claims;
import io.jsonwebtoken.Jwts;
import io.jsonwebtoken.SignatureAlgorithm;
import io.jsonwebtoken.security.Keys;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.stereotype.Service;
import java.security.Key;
import java.util.Date;
import java.util.HashMap;
import java.util.Map;
import java.util.function.Function;
@Service
public class JwtService {
// Use a secure, randomly generated key. This should be stored securely, not hardcoded.
private static final Key SECRET_KEY = Keys.secretKeyFor(SignatureAlgorithm.HS256);
private static final long JWT_EXPIRATION_MS = 1000 * 60 * 60; // 1 hour
public String extractUsername(String token) {
return extractClaim(token, Claims::getSubject);
}
public <T> T extractClaim(String token, Function<Claims, T> claimsResolver) {
final Claims claims = extractAllClaims(token);
return claimsResolver.apply(claims);
}
public String generateToken(UserDetails userDetails) {
Map<String, Object> claims = new HashMap<>();
// You can add custom claims here, e.g., roles
return createToken(claims, userDetails.getUsername());
}
public boolean isTokenValid(String token, UserDetails userDetails) {
final String username = extractUsername(token);
return (username.equals(userDetails.getUsername())) && !isTokenExpired(token);
}
private boolean isTokenExpired(String token) {
return extractExpiration(token).before(new Date());
}
private Date extractExpiration(String token) {
return extractClaim(token, Claims::getExpiration);
}
private String createToken(Map<String, Object> claims, String subject) {
return Jwts.builder()
.setClaims(claims)
.setSubject(subject)
.setIssuedAt(new Date(System.currentTimeMillis()))
.setExpiration(new Date(System.currentTimeMillis() + JWT_EXPIRATION_MS))
.signWith(SECRET_KEY, SignatureAlgorithm.HS256)
.compact();
}
private Claims extractAllClaims(String token) {
return Jwts.parserBuilder()
.setSigningKey(SECRET_KEY)
.build()
.parseClaimsJws(token)
.getBody();
}
}
Next, we create a custom filter that runs once per request to validate the token and set the security context.
package com.example.security.jwt;
import jakarta.servlet.FilterChain;
import jakarta.servlet.ServletException;
import jakarta.servlet.http.HttpServletRequest;
import jakarta.servlet.http.HttpServletResponse;
import lombok.RequiredArgsConstructor;
import org.springframework.lang.NonNull;
import org.springframework.security.authentication.UsernamePasswordAuthenticationToken;
import org.springframework.security.core.context.SecurityContextHolder;
import org.springframework.security.core.userdetails.UserDetails;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.web.authentication.WebAuthenticationDetailsSource;
import org.springframework.stereotype.Component;
import org.springframework.web.filter.OncePerRequestFilter;
import java.io.IOException;
@Component
@RequiredArgsConstructor // Lombok annotation for constructor injection
public class JwtAuthenticationFilter extends OncePerRequestFilter {
private final JwtService jwtService;
private final UserDetailsService userDetailsService;
@Override
protected void doFilterInternal(
@NonNull HttpServletRequest request,
@NonNull HttpServletResponse response,
@NonNull FilterChain filterChain
) throws ServletException, IOException {
final String authHeader = request.getHeader("Authorization");
final String jwt;
final String username;
if (authHeader == null || !authHeader.startsWith("Bearer ")) {
filterChain.doFilter(request, response);
return;
}
jwt = authHeader.substring(7);
username = jwtService.extractUsername(jwt);
if (username != null && SecurityContextHolder.getContext().getAuthentication() == null) {
UserDetails userDetails = this.userDetailsService.loadUserByUsername(username);
if (jwtService.isTokenValid(jwt, userDetails)) {
UsernamePasswordAuthenticationToken authToken = new UsernamePasswordAuthenticationToken(
userDetails,
null, // Credentials are not needed for token-based auth
userDetails.getAuthorities()
);
authToken.setDetails(new WebAuthenticationDetailsSource().buildDetails(request));
SecurityContextHolder.getContext().setAuthentication(authToken);
}
}
filterChain.doFilter(request, response);
}
}
This filter must then be added to the SecurityFilterChain before the standard UsernamePasswordAuthenticationFilter.
A Brief Look at OAuth2
For scenarios involving third-party authentication (e.g., “Sign in with Google” or “Login with GitHub”), OAuth Java implementations are the standard. OAuth2 is a framework for delegated authorization. It allows an application to obtain limited access to a user’s account on another service. Spring Security provides first-class support for implementing both OAuth2 clients and authorization servers, greatly simplifying this complex protocol.
Securing Your Application: Best Practices and Pitfalls








Implementing authentication is only half the battle; doing it securely is what matters. Adhering to Java Best Practices for security is non-negotiable.
Password Management
- Never Store Plaintext Passwords: This is the cardinal sin of security. Always hash and salt passwords.
- Use a Strong Hashing Algorithm: Use adaptive one-way hash functions like BCrypt, SCrypt, or Argon2. Spring Security’s
BCryptPasswordEncoderis an excellent choice. - Enforce Strong Password Policies: Encourage or require users to create complex passwords to protect against brute-force attacks.
JWT Security
- Use Strong Secret Keys: For symmetric algorithms (HS256), your secret key must have high entropy and be stored securely (e.g., in environment variables or a secret manager), not in source code. For asymmetric algorithms (RS256), protect your private key diligently.
- Don’t Put Sensitive Data in the Payload: The JWT payload is Base64Url encoded, not encrypted. Anyone can read it. Only include non-sensitive data like user ID and roles.
- Implement Token Expiration and Refresh Tokens: Short-lived access tokens (e.g., 5-15 minutes) limit the window of opportunity for an attacker if a token is compromised. Use long-lived refresh tokens to obtain new access tokens without requiring the user to log in again.
General Security Principles
- Use HTTPS Everywhere: Encrypt all traffic between the client and server to prevent man-in-the-middle attacks.
- Keep Dependencies Updated: Regularly scan your project’s dependencies (using tools from Java Maven or Gradle) for known vulnerabilities and update them promptly.
- Principle of Least Privilege: Ensure users and services only have the permissions absolutely necessary to perform their functions.
Conclusion
Java Authentication has evolved significantly, moving from the low-level, complex APIs of JAAS to the powerful, developer-friendly abstractions provided by Spring Security. Today, building a secure Java Backend means leveraging these modern tools to implement robust authentication patterns like token-based JWT for stateless services or OAuth2 for delegated authorization.
We’ve seen how to configure basic authentication, implement a full JWT flow in a Spring Boot application, and discussed the critical best practices that underpin a secure system. As you continue your Java Programming journey, remember that security is a continuous process. Stay informed about emerging threats and best practices, and always treat user data with the utmost care. The next steps in your learning path could be exploring fine-grained authorization with method-level security, diving deeper into OAuth2 and OpenID Connect, or investigating advanced topics in Java Cryptography.
